August 5, 2024
An issue with Foxit’s PDF Editor which causes partial redaction of information was recently identified and new releases (PDF Editor v2024.2.3, PDF Editor v13.1.3, and Mac Editor v2024.2.3) are now available. See the Security Bulletin for more details.
We recommend you take these steps as soon as possible to ensure your data continues to be securely protected.
Please note the issue occurs under the following conditions:
All 4 conditions must be met simultaneously to replicate this issue.
Security and safety are Foxit’s top priorities, and we are committed to providing our clients with a secure and reliable experience when using our products.
It is paramount that customers follow the proper implementation steps to ensure potential exploitation is blocked at the source. We appreciate the cooperation from all our customers throughout this process.
Foxit prides itself on delivering industry-leading levels of security protection for individual users as well as organizations of all sizes and industries. We recognize that our users’ information and workflows are sensitive and need the utmost protection and such, we have taken steps to address the issue. For more information, please contact Touchdown PR at [email protected].
May 23, 2024
You may have recently heard or read about a potential low-impact phishing risk related to Foxit PDF Editor and Reader that could be found in “specially crafted PDF documents”. First and foremost, Foxit wants to assure its users that their security and safety are our top priorities, and we are committed to providing a secure and reliable experience with our products. The company has already fast-tracked a fix to the issue that will be implemented within the week. The 2024.2 update for Foxit PDF Editor and Reader will also remedy this issue.
Although the 'exploit' does not meet the classic definition of triggering malicious activity, Foxit is still taking this very seriously. In short, the risk is associated with manipulating those users who skip security warnings and those that may be used to habitually clicking 'OK' without understanding the potential risks involved. Upon opening one of these "specially crafted PDF" documents, users may encounter a dialog box warning them about potential security risks associated with certain features in the document. If the user chooses to enable these features, a second dialog box may appear, cautioning that additional commands are about to be executed.
Again, a fast-tracked fix is already in the works for this issue, but in the meantime, we believe that users can easily eliminate this risk. Before opening files from unknown sources, when encountering security warnings, we encourage users to pay attention. We recommend selecting the "NO" option if users encounter the dialog box described above to ensure their security remains protected. It is also recommended that users never execute embedded code from untrusted sources, regardless of the software product.
Foxit prides itself on delivering industry-leading level of security protection for individual users as well as organizations of all sizes and industries. We recognize that our user’s information and workflow are sensitive and needs the utmost protection. Please know that we currently actioning and resolving this issue. Please feel free to contact us with any questions or if you need additional information. If users have any further questions or concerns regarding this matter, they can reach out to our support team for immediate assistance.
Dec. 17th, 2021
On December 9th, 2021, Foxit was notified of the Log4j 2 vulnerability, also referred to as LogJam or Log4Shell. Our team took swift and immediate action to mitigate any risk for our users, including application of the patch to resolve the situation as soon as it became available – patch Log4j 2.17. We have determined that no compromises were or are currently present within our software or for any of our users as a result of this activity.
We are committed to the security of our product, the privacy of our user’s data, and the transparency of our communication. For these reasons, we have strict measures in place to monitor and prevent any security breaches, as well as to implement immediate preventative and mitigative action when needed.
Our team of security experts will continue to monitor the Log4j 2 vulnerability as it develops, including implementation of heightened surveillance of any and all suspicious activity, and take any necessary actions promptly as deemed necessary and as recommended by the Cybersecurity & Infrastructure Security Agency (CISA).
What is Log4j 2?
Developed by the Apache Software Foundation, Log4j is a Java-based logging software that records events, software runs, and communications between a particular system and its users. Log4j 2 is the most recently updated version of the Apache logging software.
The security vulnerability identified with the latest Log4j 2 update could potentially allow hackers the ability to institute control over log messages and parameters, which could lead to malicious behavior and the execution of arbitrary code.
More information on the Log4j 2 vulnerability can be found here on Apache’s website and on the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) here.
What is Foxit doing to prevent any security risks or malicious acts from occurring as a result of the Log4j 2 vulnerability?
Our security team’s efforts regarding the Log4j 2 vulnerability are ongoing. So far, we have performed the following actions as determined necessary by our team and by recommendation of CISA:
What steps will Foxit continue to take in response to the Log4j 2 vulnerability?
Ongoing concentrated efforts are required at this time in response to the Log4j 2 vulnerability. We will continue to monitor the situation as it progresses and take the following actions as needed:
As a user of Foxit, am I or my business currently at risk from the Log4j 2 vulnerability?
Since learning of the vulnerability, Foxit has implemented strict monitoring of the situation and all potential risk factors. We have determined that there are currently no compromises to our software or to any of our user’s data or usage of our application.
We encourage our customers and vendors to assess individual endpoint implementations for the use of the Log4j software; this includes any third-party software.
August 30, 2019
Foxit has determined that unauthorized access to its data systems took place recently. Third parties have gained access to Foxit’s “My Account” user account data, which contains email addresses, passwords, users’ names, phone numbers, company names and IP addresses. No payment information was exposed.
Foxit’s security team has immediately launched a digital forensics investigation. The company has invalidated the account passwords for all potentially impacted accounts, requiring users to reset their passwords to regain access to the My Account service. Foxit has notified law enforcement agencies and data protection authorities and is destined to cooperate with the agencies’ investigations. In addition, the company has hired a security management firm to conduct an in-depth analysis, strengthen the company’s security posture and protect against future cyber security incidents.
Foxit has contacted all affected users and informed them about the risks and what steps to take to keep risks at a minimum. Foxit recommends its customers to not underestimate the risk of the data breach and to remain vigilant. Customers that use their Foxit “My Account” credentials on other websites or services are encouraged to change their passwords to prevent unauthorized access. Foxit also recommends customers to remain vigilant by reviewing account statements and monitoring credit reports to avoid identity theft. Customers should furthermore be aware that fraudsters may use their data to gather further information by deception (“phishing”).
Foxit’s “My Account” is a free membership service that gives customers access to software trial downloads, order histories, product registration information, and troubleshooting and support information. The system holds users’ names, email addresses, company names, IP addresses, and phone numbers, but does not hold other personal identification data or payment card information. Foxit does not keep customer credit card information in its systems. Foxit has emailed it’s My Account customers with this notification and a link to create a new and more secure password.
Security and the privacy of customer data is very important to Foxit, and the company will take all reasonable steps to ensure customer information stay secure in the future.
For further information customers can contact the data protection officer of Foxit Inc. under [email protected].
August 22, 2017
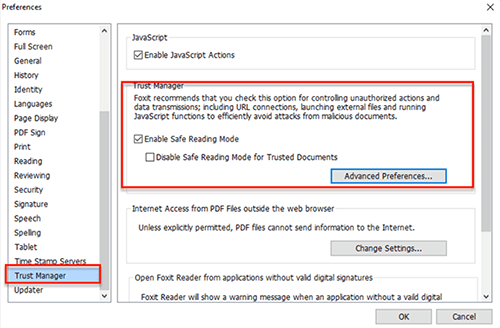
1. Nature of this Vulnerability — allowing user who is not using “Safe Reading Mode” to execute powerful JavaScript functions that can potentially cause security concerns. “Safe Reading Mode” is enabled in both PhantomPDF and Reader as a default setting, but user can disable it using preference settings.
2. How we plan to solve this problem — add an additional guard in PhantomPDF/Reader code where when opening a PDF document contains these powerful ( and thus potentially insecure) JavaScript functions, the software will check if the document is digitally signed by a verifiable/trustworthy person of entity. Only certified documents can run these powerful JS functions even when “Safe Reading Mode” is turned off.
3. When is the fix going to be ready — we plan to release a Reader/PhantomPDF 8.3.2 patch update this week (ETA Aug 25th) with additional guard against misuse of powerful (potentially insecure) JavaScript functions — this will make Foxit software equivalent to what Adobe does.
4. Who and what products are impacted — because this vulnerability can be caused by user(potential hackers) misusing powerful JavaScript functions. Only PhantomPDF and Reader users who have turn off the default setting of “Safe Reading Mode” to allow execution of JavaScript in any pdf document might get impacted. Users for other Foxit Products are not impacted by this vulnerability. For Phantom and Reader users, it’s our recommendation and out of box setting to disallow JavaScript execution until user verifies the source of document. If user continues to keep the “Safe Reading Mode” setting on, they will not be impacted.
5. How to check and re-enable “Safe Reading Mode” in PhantomPDF and Reader
For end user of PhantomPDF or Reader, please go to Preference > Trust Manager
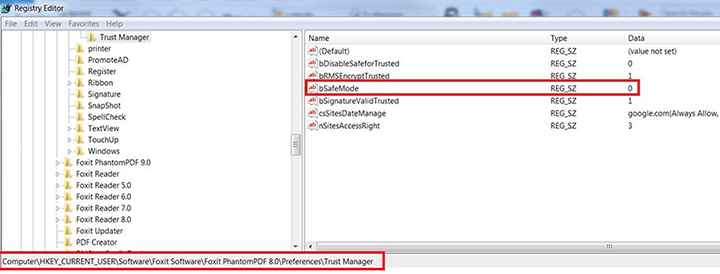
For users who want to configure thru Window's Registry
For IT or system admin who want to batch configure, please use GPO template https://cdn01.foxitsoftware.com/pub/foxit/manual/reader/en_us/FoxitEnterpriseDeploymentAndConfiguration_831.pdf
March 15, 2017
Foxit Reader is a fast, affordable, and secure way to view PDF files. Over 425 million users have already made the switch to Foxit Reader. If you are not already using Foxit to manage all your PDFs, we encourage you to upgrade today. The latest version of Foxit Reader is available on our website: https://www.foxit.com/pdf-reader/.
At the core of Foxit Reader is a secure processing engine that is also powering platforms such as Google Chrome, Google Gmail, and Amazon Kindle. Billions of people confidently exchange sensitive over these platforms.
Even in the face of continual threats from hackers and other threats, Foxit Reader is secure enough to withstand any cybersecurity attack. It is important, therefore, that you use authentic Foxit software.
Recently some of our customers alerted us about Foxit Reader being listed in Vault 7: CIA hacking tools revealed. They stated the following two new DLL hijack issues with Foxit Reader:
#1 - Foxit Reader attempts to auto update itself, looking for a DLL named “UpdateLOC.dll” from its plugins folder (\Foxit Reader\plugins).
We confirm that there’s no “UpdateLOC.dll” under its plugins folder (\Foxit Reader\plugins), so there’s no such hijack issue in Foxit Reader.
#2 - Foxit attempts to load the system DLL “msimg32.dll” adjacent to itself first (\app\Foxit Reader\) before loading it in the proper location.
We don’t attempt to load the system DLL “msimg32.dll” adjacent to itself first (\app\Foxit Reader\) as we call GetSystemDirectory() directly to get the real msimg32.dll. Foxit use a fully qualified path name when loading “msimg32.dll”, so there’s no such hijack issue in Foxit Reader.
More information about guidance for developers on how to load libraries securely can be found at https://blogs.technet.microsoft.com/srd/2010/08/23/more-information-about-the-dll-preloading-remote-attack-vector/. “While there are several affected situations, described in detail in the above MSDN article, our general recommendations are: Where possible, use a fully qualified path name when loading a library; ….”
Please don’t hesitate to contact us if you have any questions: [email protected].
May 22, 2016
Foxit© Reader is a fast, secure and inexpensive way to view PDF files. Over 400 million people have already made the switch to Foxit Reader. If you are not already using Foxit to manage all your PDFs, we encourage you to upgrade today. The latest version of Foxit Reader is available on our website: https://www.foxit.com/pdf-reader/.
At the core of Foxit Reader is a secure processing engine that is also powering platforms such as Google Chrome, Google Gmail and Amazon Kindle. Billions of people exchange sensitive over these platforms and do so confidently.
Even in the face of continual threats from hackers and other criminals, Foxit Reader is secure enough to withstand any cybersecurity attack. It is important, therefore, that you use authentic Foxit Software.
Some of our customers find it more convenient to download Foxit Reader from one of our partner sites. No matter where you are downloading our software from, be sure to confirm that Foxit Software Incorporated is identified as the verified publisher when the User Account Control popup window appears (see figure 1 below). The Foxit logo should also be included in the window.
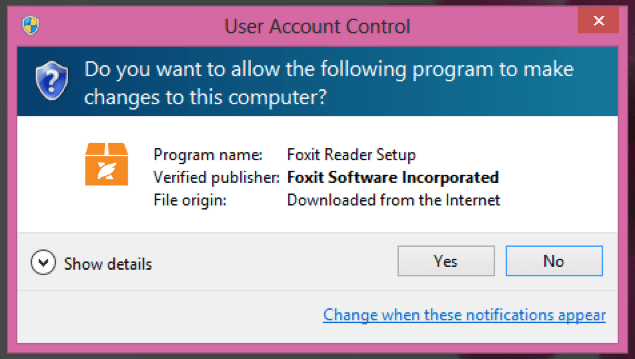
Figure 1: User Account Control popup window confirming authenticity of Foxit Reader software download
If you have previously downloaded Foxit Reader and are unsure about the authenticity of your reader, follow these steps:
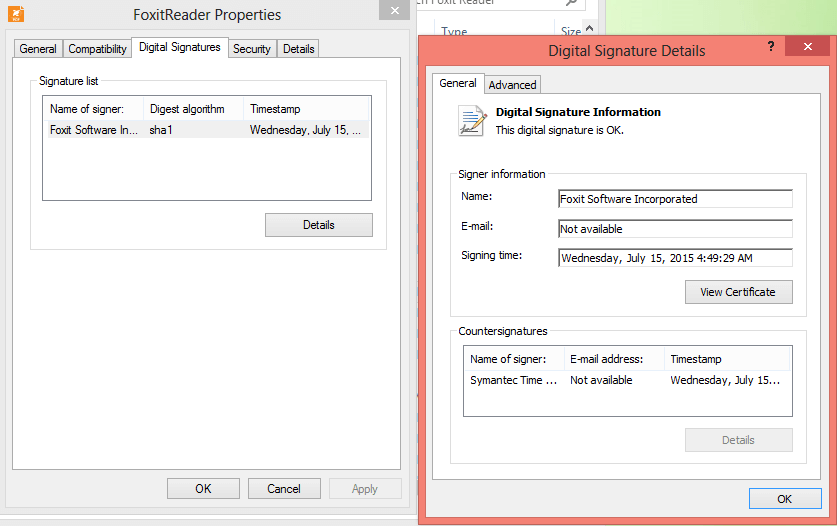
Figure 2: Digital Signature Details popup window confirming authenticity of Foxit Reader software installation
Don't risk of exposing yourself to security risks—use only genuine Foxit Software.
Please don't hesitate to contact us if you have any questions: [email protected].
March 15, 2011
On March 15, 2011 a Secunia security advisory was issued (http://secunia.com/advisories/43776/) with regards to the Foxit® Reader. The vulnerability is due to an insecure "createDataObject()" function in the JavaScript API. This insecure function allows the creation of arbitrary files with controlled content via a specially crafted PDF file. This function could be taken advantage of maliciously and compromise the security of your computer.
To protect against harm, Foxit Reader users need to update their Reader to the latest version and then enable Safe Reading Mode. The most up-to-date Foxit Reader can be installed by choosing the Help->Check for Updates Now. When the pop-up box appears, click on the Preferences box on the bottom and then enable the automatically check for Foxit updates function. Enabling Safe Reading Mode can be accomplished by choosing Tools->Preference->Trust Manager and then by clicking the option of Enable Safe Reading Mode. This can also be done during initial installation of the Foxit Reader. Safe Reading Mode enables users to control unauthorized actions and data transmissions; including URL connections, launching external files, and running JavaScript functions, to efficiently avoid attacks from malicious documents. If Safe Reading Mode is disabled, users must only open trusted PDF documents to guard against malicious attacks.
if you have any questions regarding this advisory, or any other questions, please contact Foxit by phone (+1-866-MYFOXIT or +1-866-693-6948) or enter a trouble ticket via our Support Portal.